The “DROWN Attack” is the name given to a recent vulnerability impacting on some servers running SSLv2. This page contains information on how to test for the DROWN vulnerability, with a list of further reading.
The word DROWN comes from “Decrypting RSA with Obsolete and Weakened eNcryption”.
You can quickly test your site (it’s not just web servers, it’s any service using SSLv2) for DROWN by visiting test.drownattack.com (as shown above) or by using the following URL:
https://test.drownattack.com/?site=example.com
You can also get a copy of a python utility that scans for the DROWN vulnerability here:
https://github.com/nimia/public_drown_scanner
(make sure you read the documentation, it only scans for common scenarios)
If you don’t run your own servers, your web hosting company should be addressing this for you. Estimates are that this vulnerability impacts up to 33% of the Internet. Here’s a sample of some of the top sites affected by DROWN:
- yahoo.com
- alibaba.com
- buzzfeed.com
- speedtest.net
- groupon.com
You can see the full list of the top affected sites here.
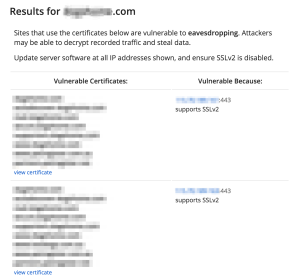
Here’s what the results look like if a site is vulnerable to DROWN:
Here’s a list of sites with more information on DROWN, I’ll update this post in the coming days to cover as much information for webmasters and system administrators as possible:
https://drownattack.com/drown-attack-paper.pdf
https://www.openssl.org/blog/blog/2016/03/01/an-openssl-users-guide-to-drown/
https://en.wikipedia.org/wiki/DROWN_attack
http://thenextweb.com/dd/2016/03/01/drown-attack-breaks-https-on-33-of-websites/
http://www.zdnet.com/article/dont-let-your-openssl-secured-web-sites-drown/