OpenSSL is a software package and developer library that programmers have used to create the systems used for encrypted communications on the majority of servers. These communication channels include a variety of services and protocols, the most common is HTTPS which is typically enabled when you purchase an SSL certificate from someone like Comodo, VeriSign/Symantec or GeoTrust.
When you access a website via HTTPS (for example https://chrisburgess.com.au), and see a padlock in your browser address bar, this indicates that a server is using a protocol called SSL (or technically SSL/TLS). A large portion of all servers using SSL rely on OpenSSL for this functionality. The OpenSSL vulnerability has nothing to do with whom you purchased the certificate from, but rather the underlying server software.
This post only covers a very simple overview of this problem, for more information please visit Heartbleed.com.
How serious is Heartbleed?
Very. In very simple terms, this vulnerability potentially allows visitors to your website to access server memory, including data that should not be accessible.
From Heartbleed.com:
Without using any privileged information or credentials we were able steal from ourselves the secret keys used for our X.509 certificates, user names and passwords, instant messages, emails and business critical documents and communication.
I use a shared host or managed VPS, is there anything I need to do to protect my website?
Even if someone else is managing your hosting, you should still update your passwords (both yours and your users). You probably don’t have access to update software on your server, however I would recommend testing your own site and opening a support ticket if you find you’re vulnerable. Most web hosts have already notified their customers of the actions they’ve taken.
I run my own server, do I need to worry about this?
Yes. You should be regularly updating your operating system and applications anyway, but this is a critical issue. It should be attended to as a priority. You should check for this vulnerability immediately.
If you are vulnerable, follow the instructions on updating OpenSSL as per your operating system release notes. These instructions will vary from system to system, and version to version. Essentially, you will be running an update/upgrade on your operating system package manager, and then restarting all services using OpenSSL (for example Apache or nginx). There are additional recommended steps beyond the scope of this post.
Should I change my passwords?
Yes. It’s recommend that you should change your passwords as a precaution. Mashable has compiled a list of affected websites:
http://mashable.com/2014/04/09/heartbleed-bug-websites-affected/
You will find that many online services will start forcing password resets.
How can I test if I’m vulnerable to Heartbleed?
You can check if a website is vulnerable to Heartbleed by visit the following sites and entering a URL:
https://lastpass.com/heartbleed/
Below is real example, to illustrate what it will look like if your server is vulnerable to Heartbleed:

Once you’ve updated your server, including OpenSSL you should see the following message. This will indicate that your website is all clear (also assuming you’ve followed all the instructions and recommendations provided by your operating system vendor/distribution).
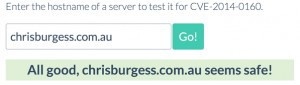
Where can I get more information?
There are dozens of insightful articles discussing Heartbleed in great detail. If you’re looking for more information, Heartbleed.com is a useful place to start.