Shellshock (or Shell Shocker) is the name given to a recent vulnerability affecting systems running the Bash shell. Bash is the default shell on most Unix/Linux systems, so it’s a big deal.
If You’re Using a Hosting Provider
Most hosting providers (all the good ones) have already either contacted their customers or posted about it on their news or blog section of their website. It’s possible that you won’t be able to run a test on your site because you don’t have access. If you’re in doubt, contact your host and ask them.
If You’re Running Your Own Servers
You should already be updating your systems regularly as best practice, so I’m assuming you’ve done that already. However, since you’re running you’re own systems, you should test to make sure you’re not vulnerable.
Manually Running Bash Commands
Rather than repeat what’s already covered on other sites, check out Further Shellshock Reading below for links where you’re find ample sample commands.
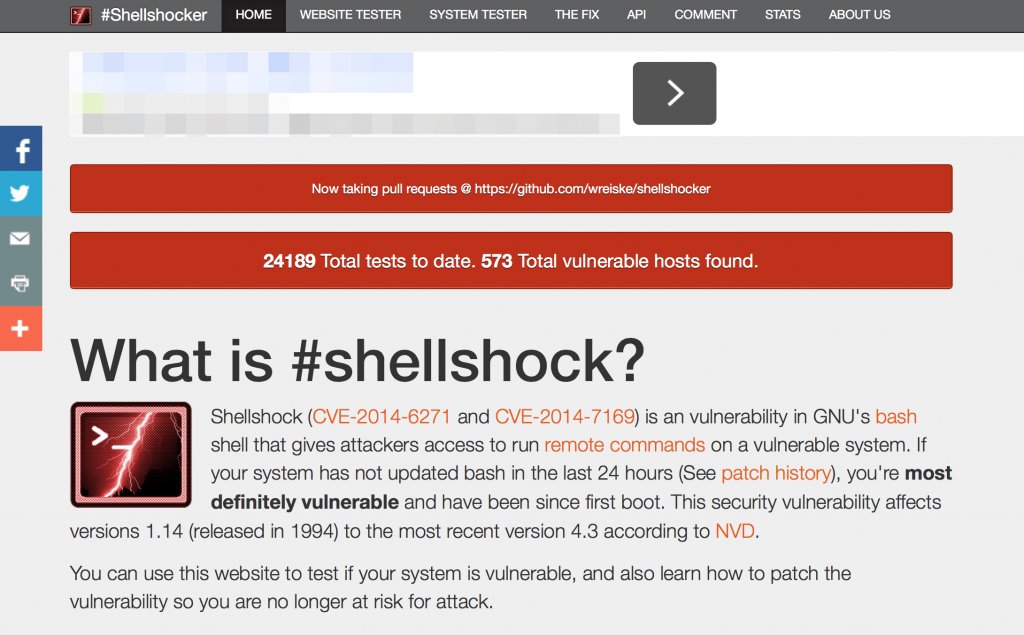
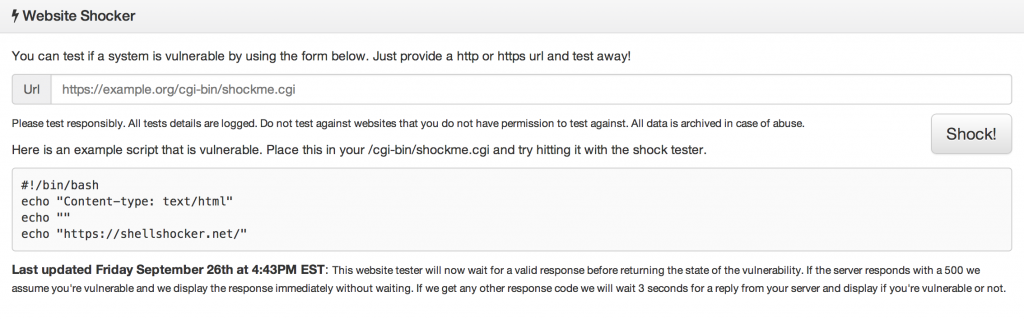
Shellshocker.net Test Site
The health IT team at Medical Informatics Engineering have created a site with instructions for checking your site. To get started, head over to shellshocker.net where they have a simple explanation of the Shellshocker Bash vulnerability as well as some instructions on different ways of testing.
Below you can see what the testing tool looks like:
Shellshock Test WordPress Plugin
ManageWP have released a WordPress plugin that checks for shell shock. At the time of writing it’s pending review to be included in the WordPress plugin directory, so you have to download it and upload to your site to install it.
Once you’ve installed the plugin, activate it:
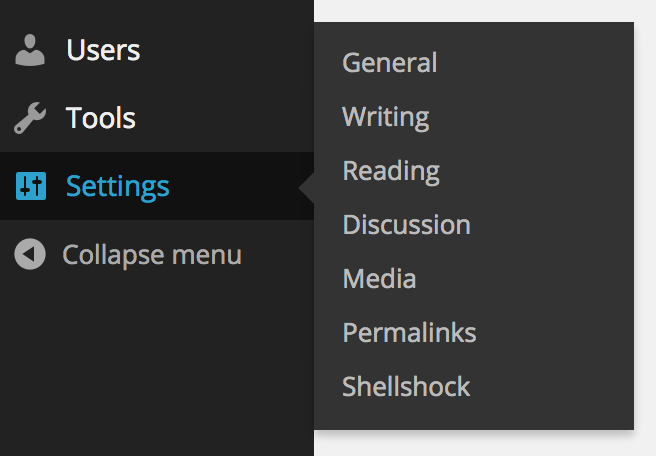
You’ll then see a new option under Settings labelled ‘Shellshock’:
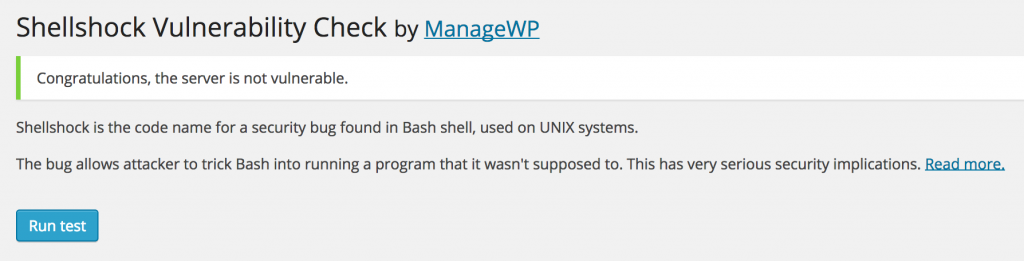
Once you’ve installed it on your website, run it and you’ll hopefully see something like this:
You can download and get more information about the ManageWP Shellshock test plugin here:
The team at ManageWP have already posted some good reading on the topic.
How to Fix the Shellshock Vulnerability
The best way to address this issue is to apply updates to your system. I’ll add pages from the common distributions below as they start getting published.
Further Shellshock Reading
If you’re looking for more information on shellshock, here are some of the best articles I’ve come across:
- http://www.troyhunt.com/2014/09/everything-you-need-to-know-about.html
- https://news.ycombinator.com/item?id=8366745
- http://blog.sucuri.net/2014/09/bash-shellshocker-attacks-increase-in-the-wild-day-1.html
Other Testing Sites
Here’s a long list of commands:
And some more testing sites and scripts:
- http://www.shellshocktest.com/
- http://bashsmash.ccsir.org/
- http://shellshock.brandonpotter.com/
- https://github.com/hannob/bashcheck
If you’re interested in web security, I’d highly recommend following the Sucuri team, their blog is always a great source of current news. You can find the Sucuri blog here.